The security challenge
As they are facing a more and more complex scenario in terms of worldwide cybersecurity, Companies struggle today to find up-to-date and solid security solutions to protect their data. The attention level on the topic is commonly quite high in most businesses, as the issue affects any kind of Company, from “one-man-bands” to the biggest Corps on the face of Earth. Companies pay attention and invest time and budgets on the issue. Do they?
While the issue is real and the counter-measures described above may sound realistic and very logic, our experience on the field tells a different truth. In fact, while many businesses are really aware of risks and solutions, many others seem to be waiting for the catastrophe before they invest real resources in preventing the second one (check for example our recent presentation on mobile interception). This said, what should those companies who already started to see the risks at the horizon do? In the present post we try to explain why information is power, in the field of security too.
Learning from TEM (Telecom Expense Management)
we can reduce risk like we reduce costs
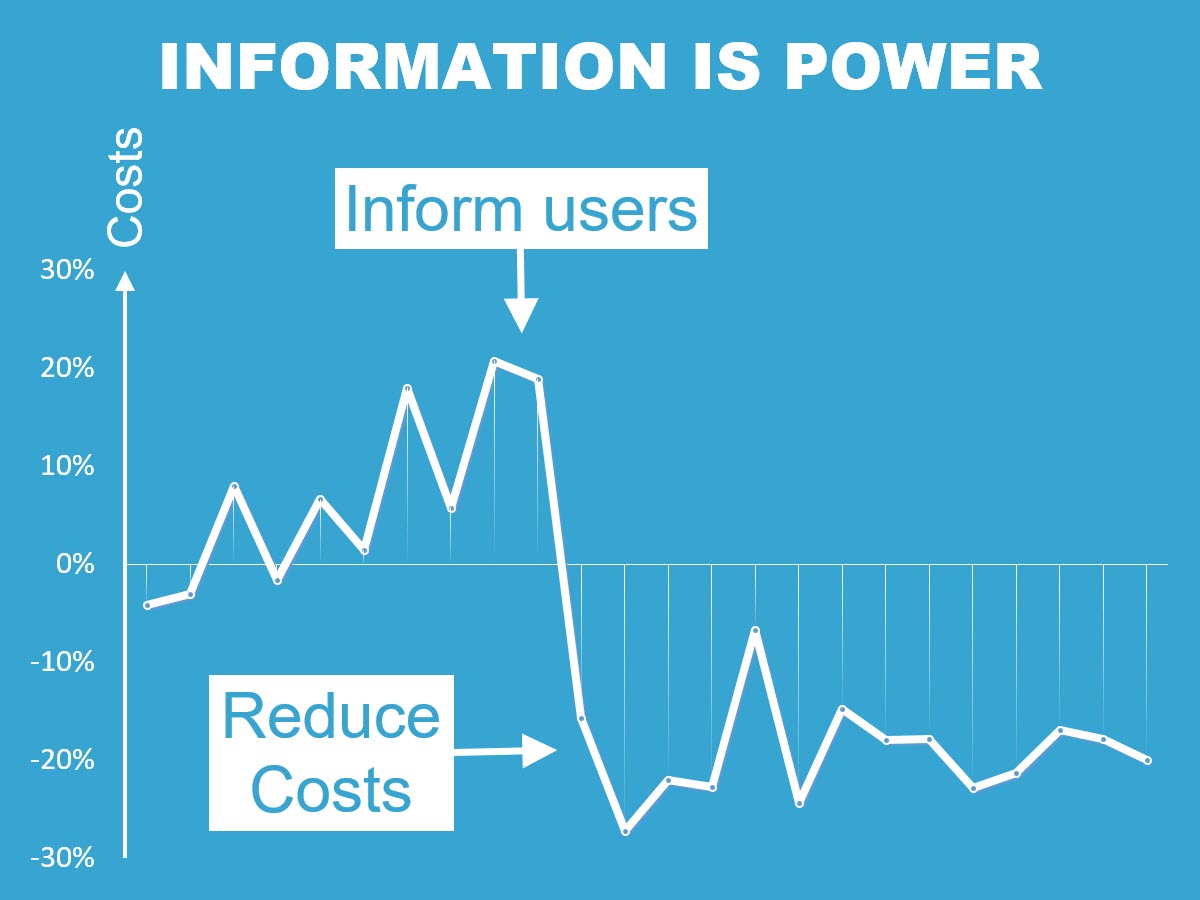
This is what happens when we implement monthly reporting to inform users about their mobile spend, as described in our post TEM reporting reduces your mobile invoice by 20%

What if the same would happen when we implement monthly reporting to inform users about their security behaviour ? An idea that can be worth considering in a context of ever increasing cyber risks.
A model which works
For many years and in many Companies we have applied models, solutions and techniques based on a simple principle: you cannot resolve a problem you don’t know it exists. In terms of costs management, this translates in structured, ad-hoc and regular reporting which dramatically emprove the awareness on the management of resources at any level, from CEO to the newest apprentice.
Through this principle we helped many Companies to move away from the old model where IT gathered costs data and scolded their colleagues from other departments with no real strategy, and we helped them to enter in a new vision where management has saving strategies, employees are aware of how they spend corporate resources and IT is simply (well, not so simply) an enabling element which gathers and (now) distributes data in form of wisely thought reports. This led in most cases in immediate cost-cutting which made Companies save around 20% of their Telecom Expenditure in the first month (check out our previous post on the topic).
Since sharing information and raising awareness levels works on the cost side, we asked ourselves: can this work with security issues too? At the end of the day, the simple principle reported above can apply at many levels and on many topics, and we increasingly noticed how security awareness is quickly moving the focus from technologies (which still play an important role) to people (who, actually, are the source of most security issues).
Daily examples of data leaks, breaches and cybercrimes help us to more and more believe that information in not only power, but security too, because we understood how people’s security is in people’s hands. Most of the time, in other people’s hands (from IT’s to cybercriminals), but a higher focus on our personal behaviour related to security risks is surely the key to success.






